The Hardening Roadmap Program
A STEP-BY-STEP PATH TO PROTECTION BASED ON REAL-WORLD BREACH EXPERIENCE
The 7 Steps in established Breach Attack pattern
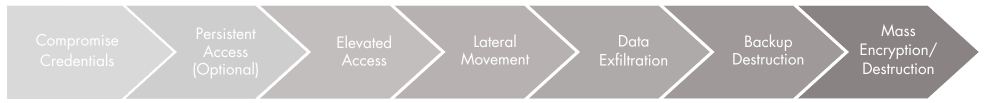
Our experience with hundreds of breach restorations has led us to conclude that while threat actors specific tactics change almost constantly, they do so along a well-established and very consistent pattern. Each step has unique vulnerabilities, and our Hardening Roadmap Program is designed to go beyond discovery and help you actually implement the steps necessary to reduce your risk and ensure your recoverability.
The Path to Protection: Reverse Engineering, beginning with Threat Actors goal (destroying your data)
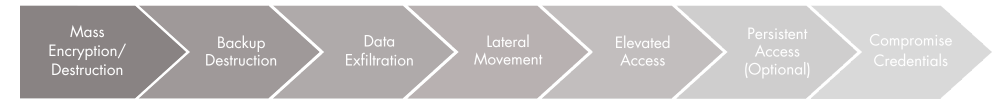
Threat Actors ultimate goal is to destroy your data, rendering your organization helpless. Our Hardening Roadmap begins by ensuring that your critical data sets are immutably backed up and will survive an attack. From there we work backwards along the breach path, shoring up vulnerabilities in each step of the path. And most important, we go beyond assessment to guide you in assessing your risk tolerance, prioritizing needed actions, and then we drive the implementation of solutions.
The Hardening Roadmap: a fundamentally different approach to protection
Typical assessments can be valuable, but too often rely just on policy configurations or product solutions – rarely taking a comprehensive view of the critical interrelationship between policies, product, people and processes. Worse, they invariably end at recommendations – which often are ignored or not implemented. In fact, our experience with breaches tells us that many breaches would have been prevented if organizations had just implemented the recommendations that they had been given. So our Hardening Roadmap program is designed to be fundamentally different. We take a holistic view of your cybersecurity products and policies as well as your people and processes, and then go beyond providing recommendations to partner with you to prioritize actions based on your risk acceptance and then guide you through implementing the needed solutions
■ Outcome focused, actionable and prioritized recommendations
■ Dedicated Hardening Coach to guide you through implementation
■ Risk Dashboard to manage the portfolio of remediation activities and identify risk acceptance to ensure business and IT alignment on decisions
Designed to change outcomes, not simply provide recommendations
■ The Hardening Roadmap is a program, not an assessment. A monthly commitment to take your organization through a step-by-step betterment plan to help ensure risk reduction and breach survivability
■ Dedicated coach and program manager to help guide decision and drive implementation of security improvements
■ Option to change priority of steps based on your needs
Please reach out to Mike Williams at 423.305.7890 or mike.williams@conversantgroup.com or your Account Executive to discuss your Betterment Plan.
