CVEs 2022-42475 and 2022-27518: Critical Severity Vulnerabilities Under Active Exploitation
On December 12, 2022, Fortinet disclosed a critical, heap-based buffer overflow vulnerability in the SSL VPN daemon on Fortinet devices. The next day, Citrix announced a critical vulnerability, also exploited in the wild, on currently supported versions of Citrix ADX and Citrix Gateway. Because these vulnerabilities have already been targeted by hackers and affect a broad range of users, they require immediate attention.
Read below to learn more about what we know today about each, how to detect whether your organization has been affected, and steps you can take immediately to help defend your systems. For the Fortinet vulnerability: If you are a Conversant customer, please reach out anytime for a FortiGate firewall inspection, impact analysis, and remediation assistance at (423) 305-7890. For the Citrix vulnerability: our fully managed services clients affected by CVE-2022-27518 need not do anything; we will contact you directly to schedule the remediation.
If you are not a Conversant customer, contact us to learn more about our services and how we can help at inquire@conversantgroup.com
Fortinet Vulnerability What We Know Today:
The new vulnerability, CVE-2022-42475, is a heap-based buffer overflow vulnerability (CWE-122) in FortiOS SSL-VPN, which may allow a remote unauthenticated attacker to conduct remote code execution over SSL VPN via specifically crafted requests. The threat actors could leverage the vulnerability to deploy malicious files on the filesystem of affected devices.
As we have seen in other campaigns affecting Fortinet appliances (CVE-2022-40684), threat actors may make use of remote code execution in Fortinet appliances to:
- Access and download the appliance’s configuration file (including cleartext rules, policies, filtering, usernames, routing configurations, as well as encrypted passwords)
- Create privileged administrator accounts
- Upload and run scripts
What Is Affected?
The following Fortinet products are affected:
FortiOS Version 7.2.0 to 7.2.2
FortiOS version 7.0.0 to 7.0.8
FortiOS versions 6.4.0 to 6.4.10
FortiOS versions 6.2.0 to 6.2.11
FortiOS-6K7K version 7.0.0 to 7.0.7
FortiOS-6K7K version 6.4.0 to 6.4.9
FortiOS-6K7K version 6.2.0 to 6.2.11
FortiOS-6K7K version 6.0.0 to 6.0.14
What You Can Do
Look for the below indicators of compromise:
Multiple log entries with:
Logdesc=”Application crashed” und msg=”[…] application:sslvpnd,[…], Signal 11 received, Backtrace: […]”
Presence of the following artifacts in the file system:
/data/lib/libips.bak
/data/lib/libgif.so
/data/lib/libiptcp.so
/data/lib/libipudp.so
/data/lib/libjepg.so
/var/.sslvpnconfigbk
/data/etc/wxd.conf
/flash
Connections to suspicious IP addresses from FortiGate:
188.34.130.40:444
103.131.189.143:30080,30081,30443,20443
192.36.119.61:8443,444
172.247.168.153:8033
Take Action:
If you find evidence of infection, you must clean the system using FortiOS clean install. Fortinet recommends updating the affected products below to the corresponding updates.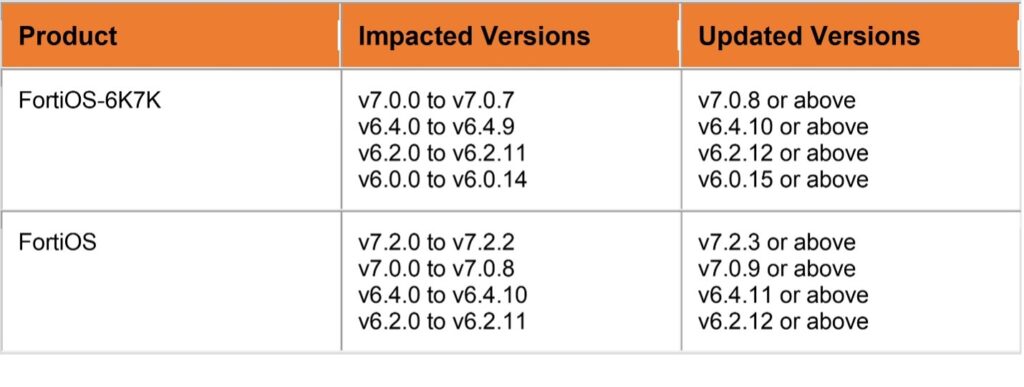
Citrix Vulnerability What We Know Today:
The new Citrix vulnerability, CVE-2022-27518, if exploited, could allow an unauthenticated remote attacker to perform arbitrary code execution on the appliance.
The following supported versions of Citrix ADC and Citrix Gateway are affected by this vulnerability:
- Citrix ADC and Citrix Gateway 13.0 before 13.0-58.32
- Citrix ADC and Citrix Gateway 12.1 before 12.1-65.25
- Citrix ADC 12.1-FIPS before 12.1-55.291
- Citrix ADC 12.1-NDcPP before 12.1-55.291
Citrix ADC and Citrix Gateway version 13.1 is unaffected. This alert only applies to customer-managed Citrix ADC and Citrix Gateway appliances. Customers using Citrix-managed cloud services or Citrix-managed Adaptive Authentication do not need to take any action.
Customers can determine if their Citrix ADC or Citrix Gateway is configured as a SAML SP or a SAML IdP by inspecting the ns.conf file for the following commands:
add authentication samlAction
– Appliance is configured as a SAML SP
OR
add authentication samlIdPProfile
– Appliance is configured as a SAML IdP
If either of the commands are present in the ns.conf file and if the version is an affected version, then the appliance must be updated.
What You Should Do
- We (and Citrix) strongly urge affected customers of Citrix ADC and Citrix Gateway to install the relevant updated versions of Citrix ADC or Citrix Gateway as soon as possible:
- Citrix ADC and Citrix Gateway 13.0-58.32 and later releases
- Citrix ADC and Citrix Gateway 12.1-65.25 and later releases of 12.1
- Citrix ADC 12.1-FIPS 12.1-55.291 and later releases of 12.1-FIPS
- Citrix ADC 12.1-NDcPP 12.1-55.291 and later releases of 12.1-NDcPP
Please note that Citrix ADC and Citrix Gateway versions prior to 12.1 are end of life (EOL), and customers on those versions are recommended to upgrade to one of the supported versions.
For any and all assistance with detection of these vulnerabilities, patching, remediation, or managed security services to defend against future threats, contact Conversant Group for end-to-end security assistance.
Have an issue? Need support? Contact Conversant Group
technical support team today:
support@conversantgroup.com
1-423-305-7890 (during business hours)
1-423-305-7890 / option 2 (after hours/weekends)










